Introduction
Codesealer Enterprise is a powerful reverse proxy designed to secure delivery and communication for modern distributed web and mobile applications. This guide covers everything you need in order to install, operate and maintain Codesealer Enterprise.
Before you start using Codesealer Enterprise, it's a good idea to get an understanding of the product. This can be done by reading the What is Codesealer? section. To get an understanding of how Codesealer can be deployed into your infrastructure, take a look at the Deployment section. If you want to take deep dive into how Codesealer works, take a look at the Architecture section.
The Installation section explains how to install the various components of the system, while the Configuration details the settings of each component. Once Codesealer Enterprise is up and running, refer to the section on the Management Portal for instructions on how to use the system.
What is Codesealer Enterprise?
Codesealer Enterprise is a powerful reverse proxy designed to secure delivery and communication for modern distributed web and mobile applications. It provides an invisible protective layer that can be deployed effortlessly into existing architectures in order to safeguard online services and ensure that end users are protected from attacks.
With Codesealer Enterprise, businesses can mitigate security risks such as
- Man-in-the-Middle attacks,
- Man-in-the-Browser attacks,
- Information gathering,
- Active code manipulation,
which can compromise the integrity and confidentiality of sensitive data. By protecting against these and other types of attacks, Codesealer Enterprise offers a comprehensive solution for enhancing the security of online services.
What does Codesealer Enterprise do?
Under normal circumstances, a web application is only protected at the transport layer by TLS. This means that everything that happens on the client side i.e., in the end user's browser, is clearly visible. This includes application code, data input by the user, and requests made by the application. If the end user's device is compromised, or if the end user themselves has malicious intentions, then the browser cannot be considered a secure environment.
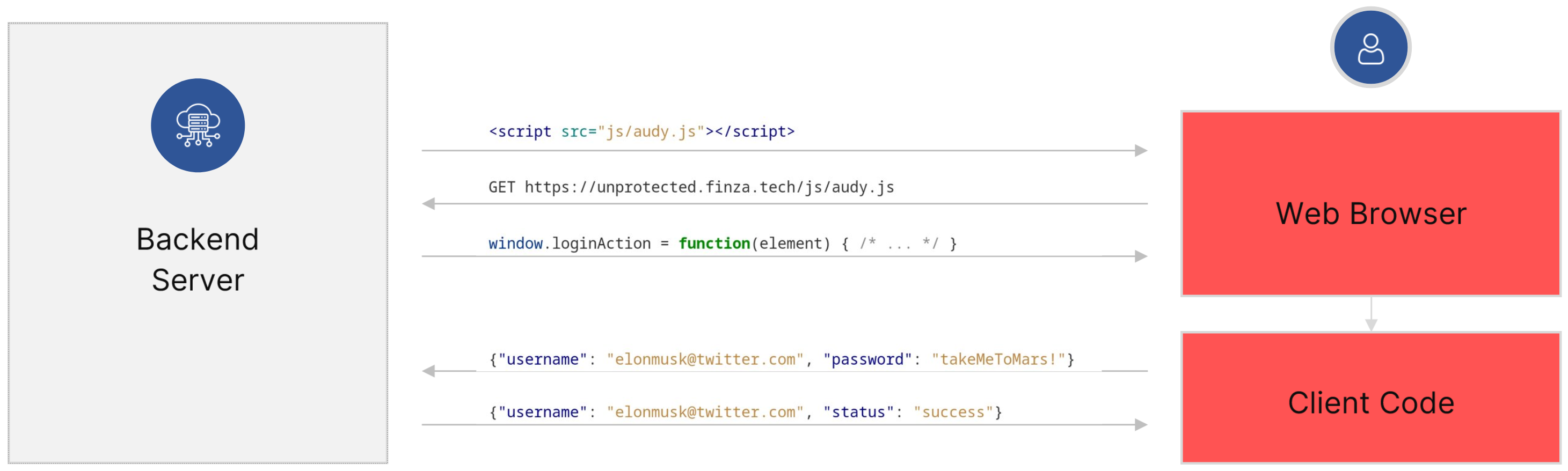
This can clearly be a problem for the end user, as an infected device can trivially lead to stolen credentials. But it also allows malicious users to easily probe the application code and the backend's API looking for vulnerabilities.
To solve these problems, Codesealer Enterprise can be deployed as a reverse proxy in front of the backend server. When a website is requested through the reverse proxy, Codesealer Enterprise will replace any application code with a Bootloader. This Bootloader is responsible for verifying the safety of the execution environment and establishing secure communication with the backend. It will fetch the application code over an encrypted channel and make sure it stays encapsulated while it is executed.

The flow of running the web application then becomes:
- The main HTML document is transferred to the web browser, containing a new and unique Bootloader instance.
- The Bootloader establishes a secure channel with the reverse proxy and fetches application code.
- The application code is launched securely, ensuring the safety and confidentiality of sensitive data.
- The Bootloader replaces any subsequent XHR or fetch calls with an encrypted variant called ANP, ensuring that dynamically loaded content is also protected.
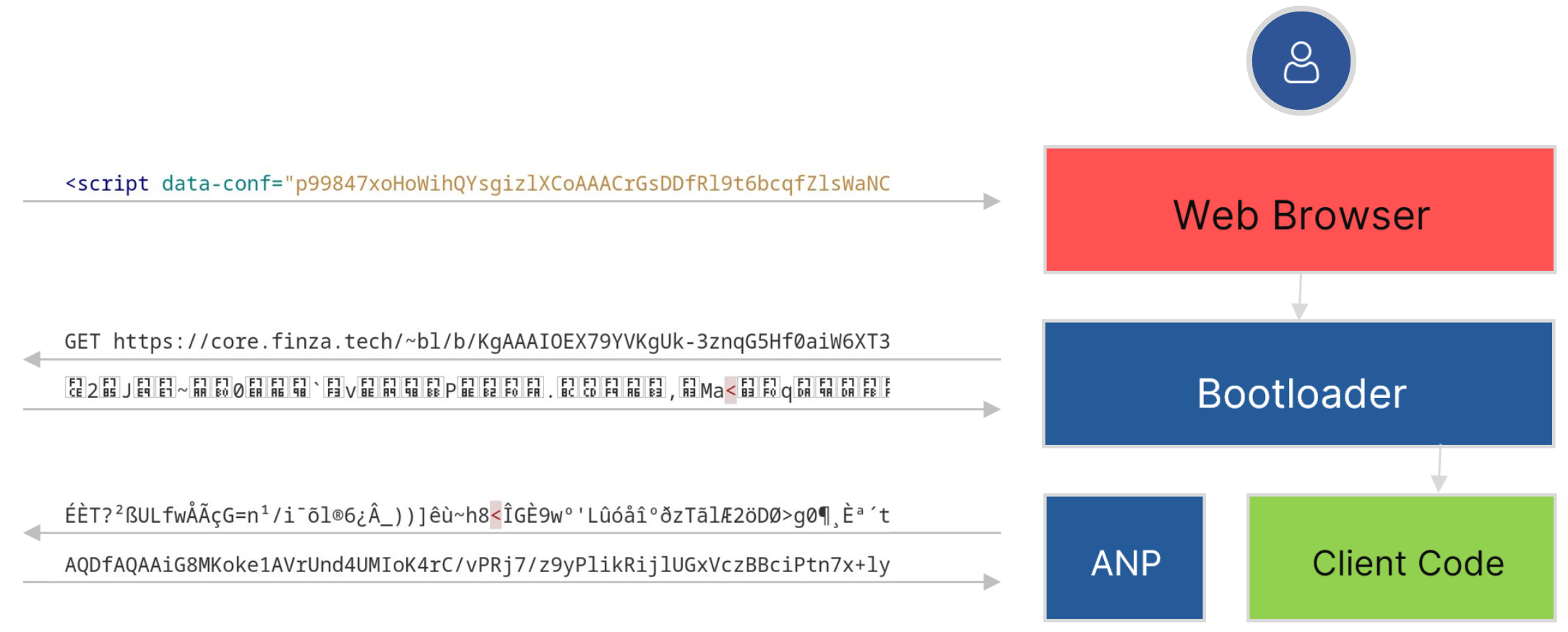
With Codesealer Enterprise, all client code is effectively encapsulated, providing enhanced security for all interactions with the Web browser and the outside world, without imposing any requirements on the end user's environment or modifications to the application code.
Deployment
A Codesealer Enterprise deployment consists of a few different components and can be configured in various different ways that provide flexibility when integrating the solution into existing architectures.
A deployment consists of:
- A Management Portal where the deployment can be configured through a web interface.
- A number of Workers (the reverse proxy itself) that provide the actual functionality.
- A Redis cluster, used for coordination between the components.
- Optionally an InfluxDB instance that provides metrics that are viewable in the Management Portal, such as requests-per-second, response times, and errors. Ideal for integration with existing monitoring solutions.
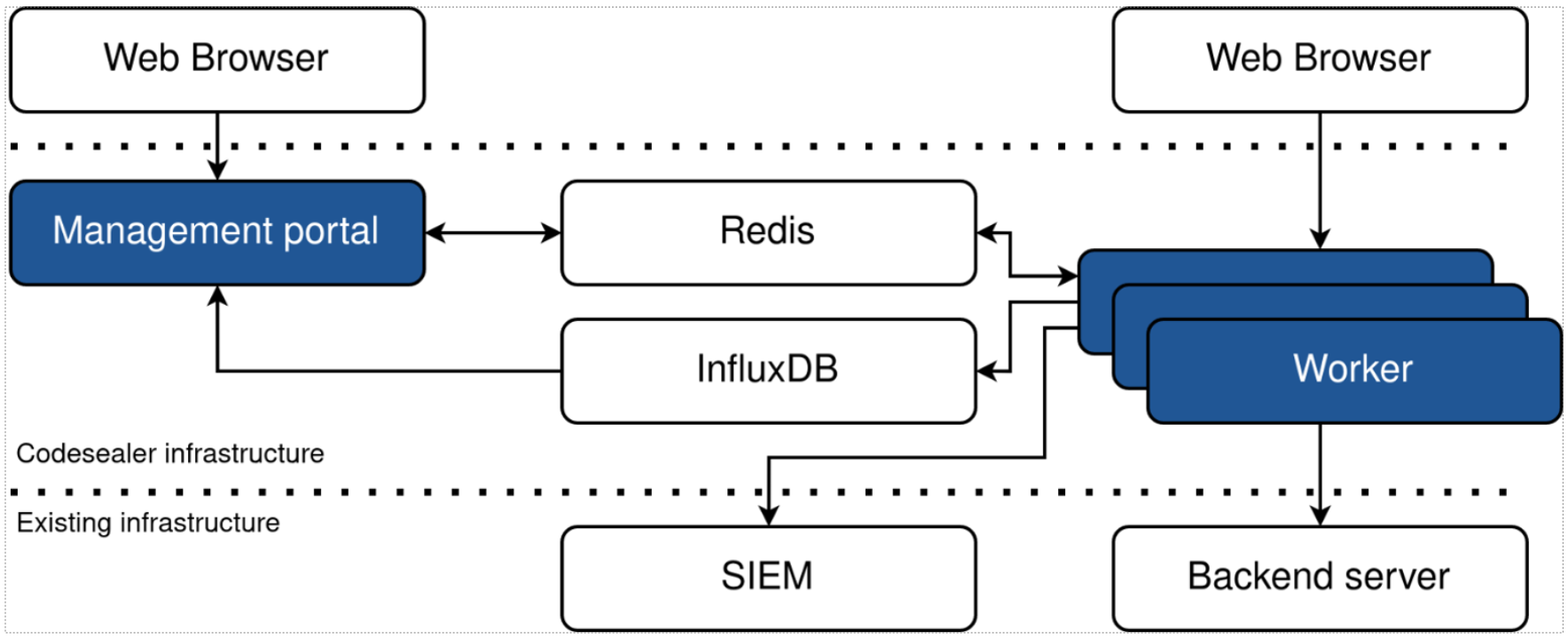
The Workers themselves can be integrated into existing architectures in various different ways:
- Workers can be located on the existing backend servers to minimize infrastructure changes with no additional resource allocation.
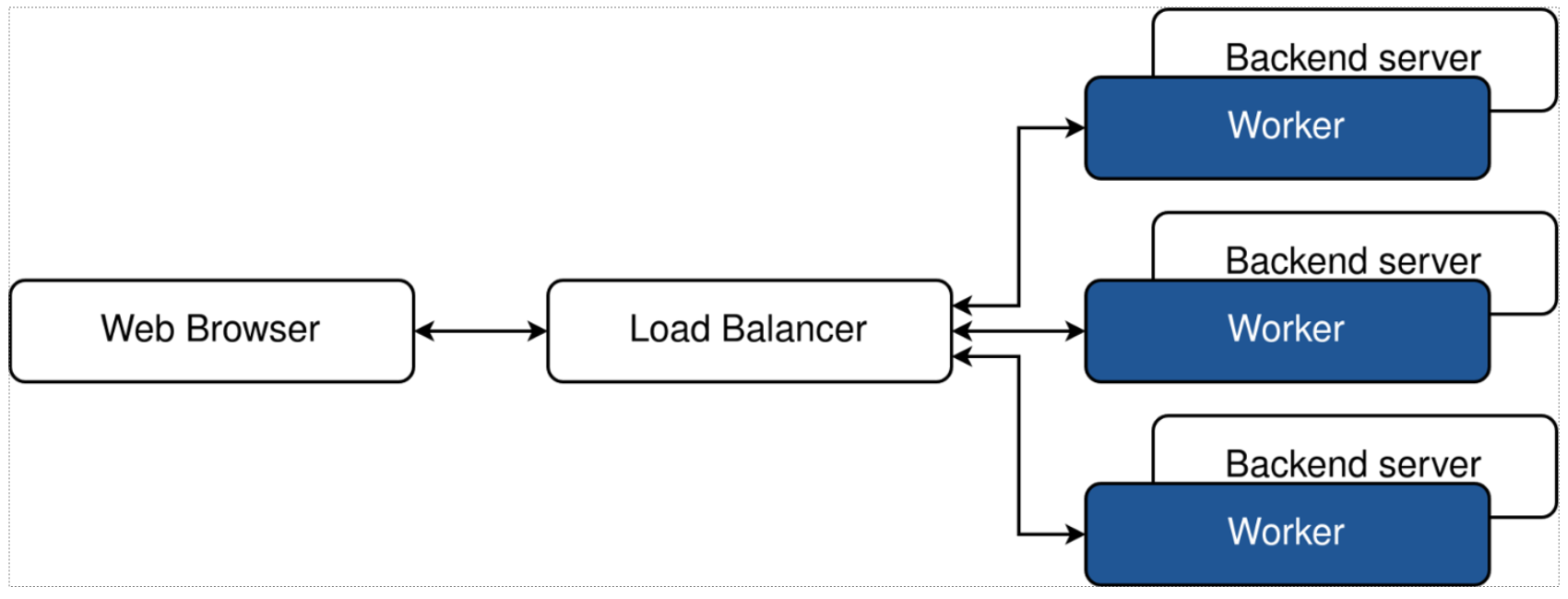
- Separate 1:1 workers can be located on dedicated instances to allow for independent maintenance without the cost of additional load balancers.
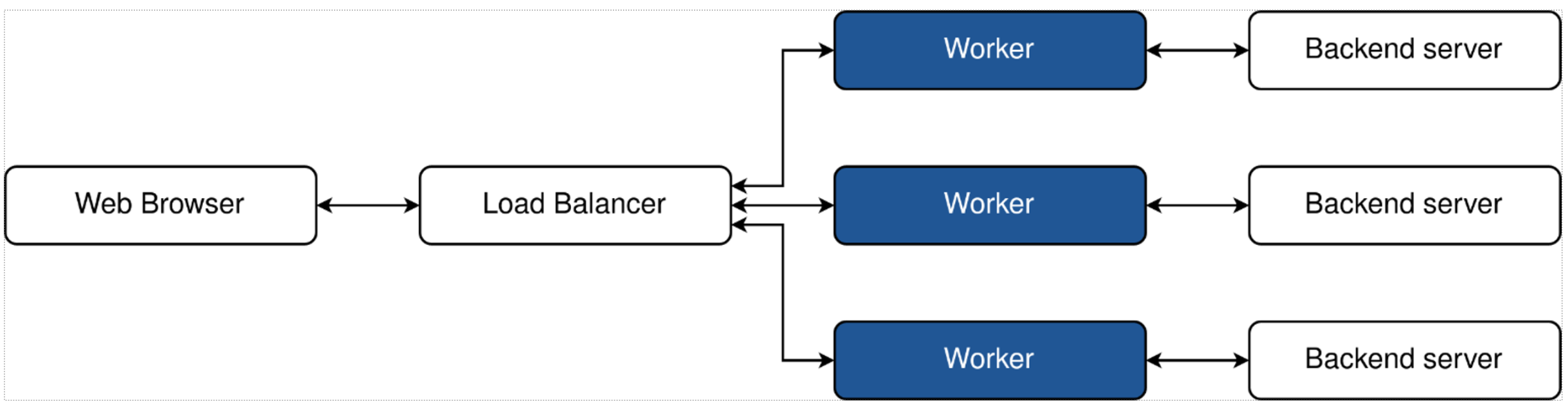
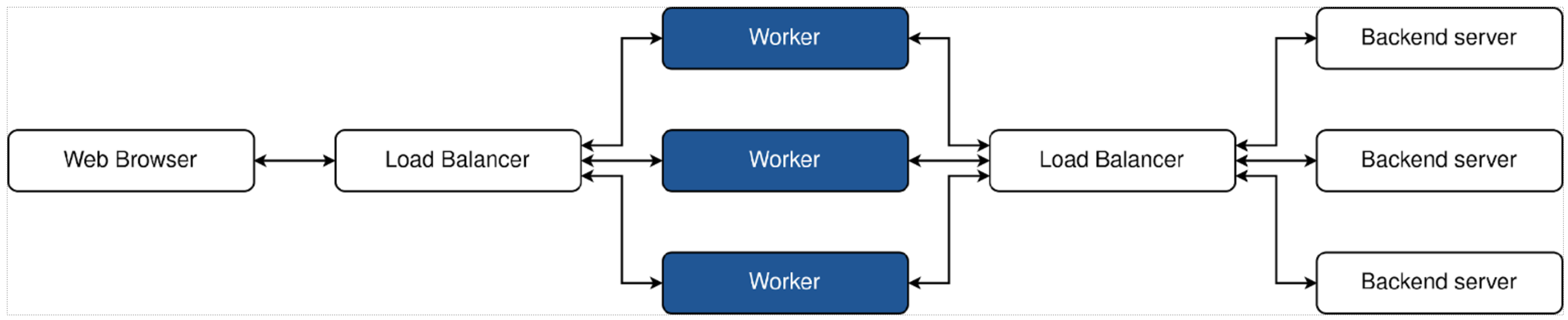
- Worker instances can be decoupled for completely independent scaling.
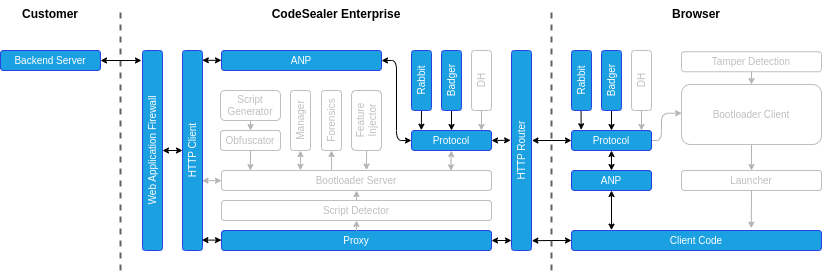
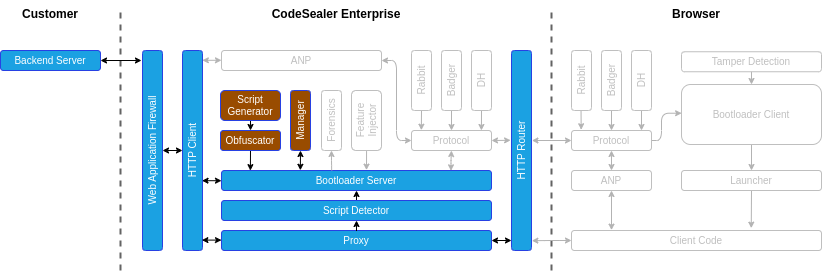
Technical Architecture
This section describes the high level-architecture of the Codesealer Enterprise reverse proxy. The diagram below shows the various components of the solution.
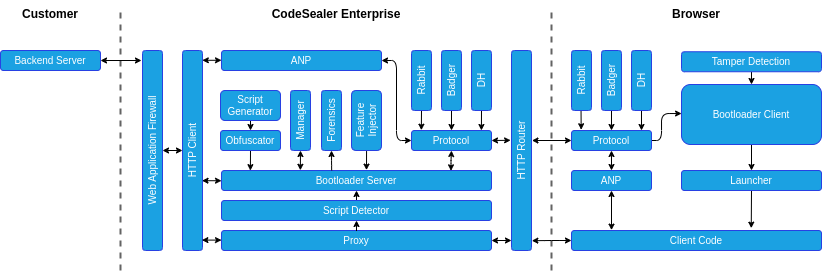
The process of protecting a web applications proceed in five phases:
- Replacing applications scripts,
- Initialising the bootloader,
- Encrypted script delivery,
- Application code execution,
- Application network protection.
Phase 1: Replacing application scripts
- When the Codesealer proxy receives a request for an HTML document, the Script Detector identifies any application scripts in the response from the backend server and registers it as an Application Script.
- A new Bootloader Instance is generated containing information about the detected Application Scripts. Each Bootloader instance is dymanically obfuscated, contains a unique version of the communication protocol, and is only valid for a limited time.
- The original script tag for the Application Script is replaced with the Bootloader instance in the HTML document, and the result is served to the browser.
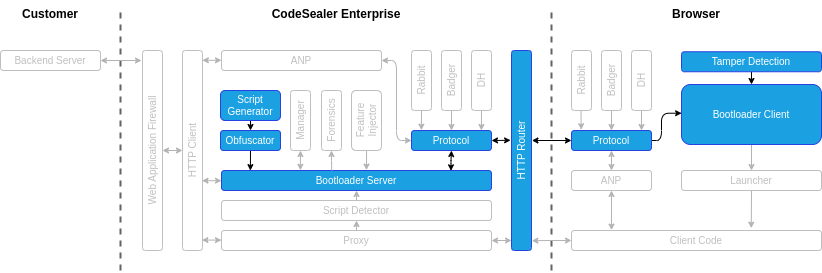
Phase 2: Initialising the bootloader
- The browser receives the Bootloader code and starts executing the Bootloader Client.
- From this point on, the Bootloader Client performs various tamper detection steps to ensure that the environment can be trusted throughout the execution.
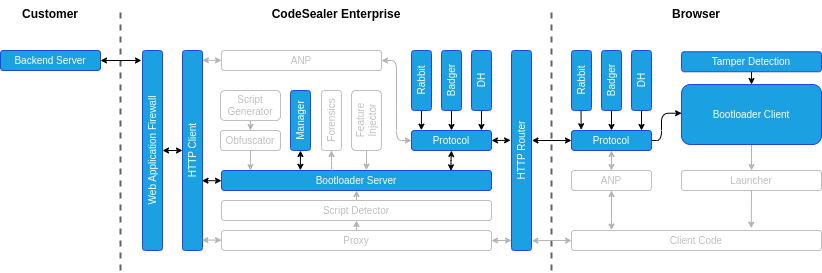
Phase 3: Encrypted script delivery
- The Bootloader Client performs a Diffie-Hellman Key Exchange and with the Codesealer Enterprise proxy server in order to establish a shared secret key.
- The Bootloader Client starts requesting all the registered Application Scripts. Each Application Script is encrypted with a random key, which in turn is encrypted with the secret key established above.
- The encrypted Application Script response is sent to the Bootloader Client.
Phase 4: Application code execution
- The Bootloader Client decrypts and authenticates each Application Script.
- If the Application Scripts pass the checks, the Bootloader starts executing the scripts.
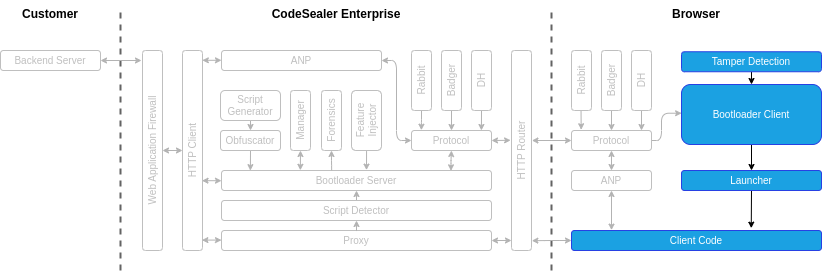
Phase 5: Application network protection
- If the Application Scripts perform any dynamic updates of the page using XHR or fetch requests, these will be intercepted by the Application Network Protection (ANP).
- ANP will encrypt the requests and send them to the reverse proxy.
- The reverse proxy will in turn decrypt the received ANP requests, proxy them as usual, and encrypt the response before sending it back to the browser.
- Once the encrypted response is received, the Bootloader will decrypt it and execute any code contained in the response.